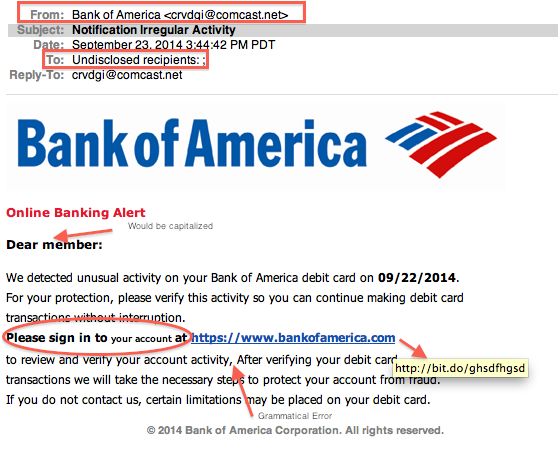
Most Businesses Won’t Survive a Disaster. Could Yours?
Most Businesses Won’t Survive a Disaster. Could Yours? With the crazy weather we’re seeing, natural disasters on the rise and cyber terrorism echoing for years, it’s not a case of ‘if’ a disaster will strike your business, but ‘when’. Surprisingly, it’s not the scope and scale of the event that influences how deeply your business is impacted, it’s your business continuity plan. Put simply, this is the all-important set of precautions and pre-planned responses to an event, laid out in bullet-proof detail and implemented with one driving focus: keeping your business running with little or no downtime. Think about what would happen if your business was hit by a natural disaster tomorrow. Would it survive? How much downtime would it take to push you into dangerous territory? According to an IBM study of all the companies that had a major loss of data, 43% never reopen, 51% close within two years and just 6% will survive long-term. For a fraction of those survivors, business eve